Two-factor authentication (2FA) has long been considered a critical defense against unauthorized access to online accounts. However, requiring both a password and a secondary verification code, often delivered via SMS, can be inconvenient and even unreliable. Google is revolutionizing account security by offering a simpler, more secure approach for high-risk accounts – phone-centric authentication.
The Password Paradox: Security vs. Convenience
For many users, the traditional password system presents a dilemma. Image 1 depicts this struggle. Creating strong, unique passwords for every account is crucial, but remembering them all can be a challenge. Weak, reused passwords make accounts vulnerable to hacking. Additionally, SMS-based 2FA codes can be intercepted by attackers, jeopardizing account security.
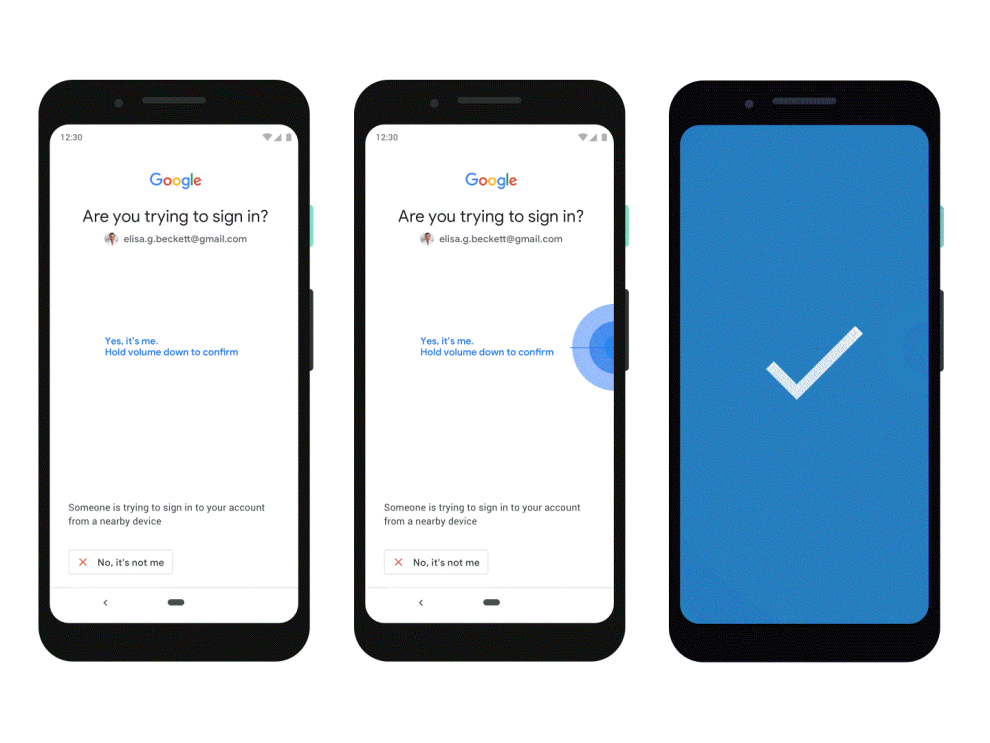
The inconvenience of traditional 2FA methods often leads users to disable it altogether, leaving their accounts exposed. Image 2 showcases a more convenient alternative – unlocking a phone with facial recognition. Google’s phone-centric authentication aims to bridge this gap, offering robust security without sacrificing ease of use.
A Stronger Shield: How Phone-Centric Authentication Works
Google’s phone-centric authentication leverages the ever-present smartphone to streamline the login process for high-risk accounts. Here’s a breakdown of how it works:
-
Enrollment: Users first need to enroll their trusted phone with their Google account. This involves verifying phone ownership through a secure process.
-
Login with Your Phone: When attempting to log in from a new device or location, Google will send a notification directly to the user’s enrolled phone.
-
Simple Approval: Users simply need to approve the login attempt on their phone using a familiar method, such as fingerprint or facial recognition, eliminating the need for separate codes.
This approach eliminates the vulnerabilities associated with SMS-based 2FA while offering a more seamless user experience. With your phone acting as the primary authentication factor, the need to remember complex passwords or manage separate codes is significantly reduced.
Prioritizing Security: Who Benefits from Phone-Centric Authentication?
While phone-centric authentication offers a convenient login experience, it’s initially being rolled out for high-risk accounts. Here’s why this targeted approach makes sense:
-
Enhanced Protection for Vulnerable Accounts: High-risk accounts, such as those containing sensitive financial information or intellectual property, require the strongest possible security measures. Phone-centric authentication adds an extra layer of defense against unauthorized access attempts.
-
A Gradual Rollout: By focusing on high-risk accounts first, Google can gather valuable feedback and ensure the system functions flawlessly before potentially offering it to all users.
-
Addressing User Concerns: Some users might be wary of relying solely on their phones for authentication. The initial rollout on high-risk accounts allows Google to address these concerns and build user trust in the new system.
Phone-centric authentication represents a significant step forward, but it’s important to remember that no security system is foolproof. Here are some additional security best practices to consider:
-
Keep Your Phone Secure: Use a strong screen lock on your phone and enable features like find my device to ensure its security.
-
Beware of Phishing Attacks: Remain vigilant against phishing attempts that try to trick you into revealing login credentials.
-
Monitor Account Activity: Regularly review your account activity for any suspicious login attempts.
By combining phone-centric authentication with these practices, you can significantly enhance your online security posture.
The Future of Logins: A Passwordless Paradise?
The introduction of phone-centric authentication signals a potential shift towards a passwordless future. Here’s what this paradigm shift might entail:
-
Biometric Authentication Takes Center Stage: Fingerprint, facial recognition, and iris scanning could become the primary methods for verifying user identity, eliminating the need for passwords altogether.
-
Improved Convenience: A passwordless login system would offer unparalleled convenience, allowing users to access their accounts with just their phones.
-
Security Concerns Remain: While biometric authentication offers advantages, potential vulnerabilities like deepfakes or stolen phone data need to be addressed to ensure a truly secure passwordless future.
The journey towards a passwordless future is still ongoing, but Google’s phone-centric authentication marks a significant step in that direction. As technology advances and security concerns are addressed, we might soon see a world where passwords become a relic of the past.
















Add Comment