Cybersecurity firm McAfee has uncovered a sophisticated malware operation that successfully planted 15 predatory loan apps on the Google Play Store, accumulating over 8 million downloads. The malicious apps, known collectively as SpyLoan, primarily targeted vulnerable users in South America, Southeast Asia, and Africa.
This latest discovery comes despite Google’s recent efforts to combat such threats and follows a similar incident in December 2023, when authorities removed another batch of SpyLoan apps that had reached 12 million downloads. The persistence of these attacks raises serious concerns about the effectiveness of current app vetting processes.
The SpyLoan scheme operates under the guise of legitimate financial assistance, offering seemingly attractive quick loans to users in developing regions. However, these apps serve as sophisticated data collection tools that harvest sensitive personal information while subjecting victims to aggressive harassment and extortion tactics.
According to McAfee’s investigation, the malware’s reach was particularly extensive in several developing markets. The most popular infected apps, including “Préstamo Seguro-Rápido” and “Préstamo Rápido-Credit Easy,” each achieved one million downloads, primarily targeting users in Mexico and Colombia respectively. Similar successful infiltrations were recorded in Thailand, Indonesia, and Senegal, with multiple apps reaching the million-download milestone.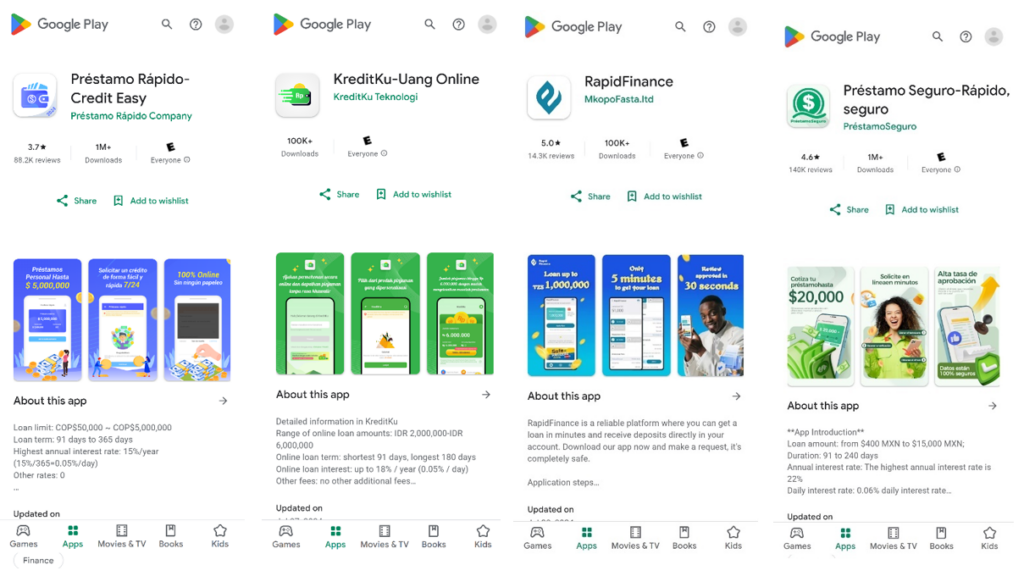
The technical sophistication of these malicious apps is noteworthy. After installation, they employ a clever validation system using one-time passwords (OTP) to verify that users are in targeted regions. The apps then begin their invasive data collection process, requiring users to submit extensive personal information including identification documents, employment details, and banking information.
What makes these apps particularly dangerous is their aggressive exploitation of device permissions. McAfee’s analysis revealed that the malware collects an alarming range of sensitive data, including complete access to SMS messages, GPS location data, network information, device details, operating system information, and even sensor data. This comprehensive data gathering serves a sinister purpose: providing ammunition for subsequent harassment and extortion attempts.
The predatory nature of these operations becomes apparent once victims receive their loans. Users find themselves trapped in cycles of high-interest payments while facing relentless harassment. The operators weaponize the stolen personal data, extending their intimidation tactics to victims’ family members found in the harvested contact lists.
This incident has exposed ongoing vulnerabilities in Google Play’s security measures. Despite Google’s partnership with McAfee through the App Defense Alliance and the implementation of various app review mechanisms, these malicious apps successfully circumvented the platform’s safeguards. The situation underscores the sophisticated nature of modern mobile malware and the challenges faced by app store operators in detecting and preventing such threats.
Security experts recommend several protective measures for mobile users. These include carefully reviewing app ratings and user feedback, researching developer credentials, and maintaining a cautious approach to app permissions. The importance of keeping Google Play Protect active on devices has also been emphasized as an essential security layer.
The widespread impact of this campaign serves as a stark reminder of the evolving nature of mobile threats and the particular vulnerability of users in developing regions to financial scams. As cybercriminals continue to adapt their tactics, the incident highlights the critical need for strengthened app store security measures and increased user awareness about the risks of installing financial apps from unknown developers.
While Google has now removed these malicious apps from the Play Store, the incident raises questions about the long-term effectiveness of current security protocols and the need for more robust screening processes to protect users from sophisticated financial fraud schemes. The continuing presence of such threats, even after previous enforcement actions, suggests that more comprehensive solutions may be needed to address this persistent security challenge.
















Add Comment