IT administrators worldwide have faced a daunting challenge: widespread account lockouts caused by false positives in Microsoft Entra ID’s newly rolled-out “leaked credentials” detection application, MACE. The issue erupted overnight, affecting countless organizations and leaving administrators scrambling to resolve the chaos. While the problem appears to stem from a glitch in the MACE Credential Revocation feature, its impact has been significant, prompting concerns about the reliability of Microsoft’s identity and access management tools.
A Nightmarish Start to the Week
Last night marked the beginning of a chaotic ordeal for IT professionals. Suddenly, numerous Windows administrators began receiving flood alerts from Microsoft Entra ID, warning them that user accounts had been flagged for having leaked credentials. The alarming messages came in waves, triggering automatic lockouts across entire organizations. Some administrators initially suspected foul play, fearing their systems had been breached. However, closer inspection revealed no signs of compromise—no unusual login attempts, no suspicious activity, and no breaches detected by external monitoring services like Have I Been Pwned (HIBP).
Reddit threads quickly lit up with reports from distressed IT teams. One administrator described the situation succinctly: “Us as well… about 1/3rd of our accounts got locked out about ~1 hour ago. We’re a Managed Service Provider (MSP), so I’m assuming this is happening to our clients as well.” Another commenter echoed similar sentiments, detailing how their organization also experienced mass lockouts without any evidence of actual compromise.
The scope of the issue became even clearer when an MDR (Managed Detection and Response) provider chimed in, reporting they had received over 20,000 notifications from Microsoft overnight regarding leaked credentials across multiple customers. The sheer volume of alerts painted a grim picture of the extent of the problem, suggesting it wasn’t isolated to a single organization but rather a systemic issue affecting enterprises globally.

A Deeper Dive into the Problem
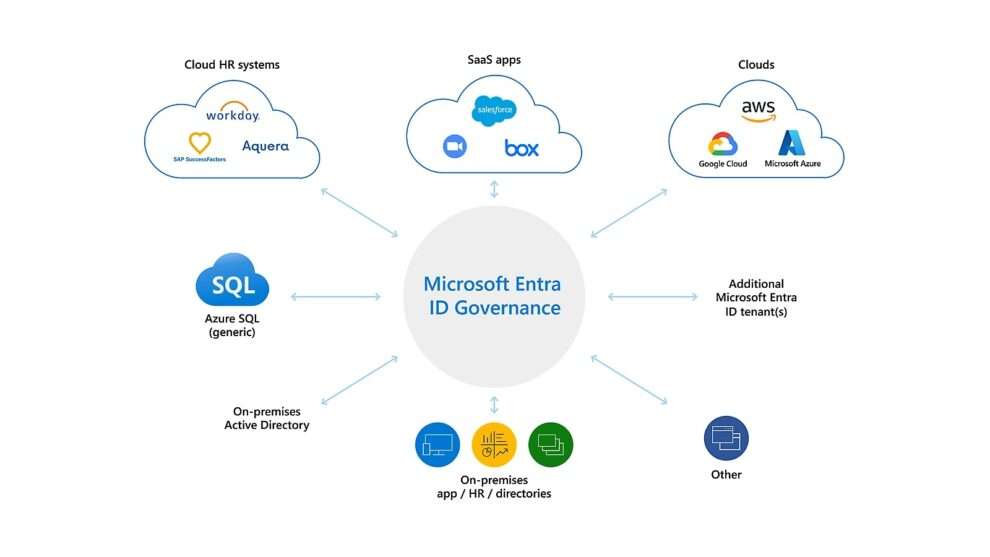
To understand the root cause of these lockouts, let’s unpack the role of MACE (Microsoft Authenticator Credential Evaluation). Introduced as part of Microsoft Entra ID, MACE is designed to detect leaked credentials and automatically lock out potentially compromised accounts. While this feature aims to enhance security, its implementation appears to have introduced unintended consequences.
According to reports from affected organizations, the lockouts coincided with the silent addition of the MACE Credential Revocation application to tenants. This timing strongly suggests a direct correlation between the introduction of MACE and the surge in false-positive alerts. Administrators who dug deeper into the situation discovered that the alerts were triggered by Error Code: 53003, a conditional access policy error linked to MACE.
Microsoft engineers later confirmed that the issue stemmed from a glitch in the MACE rollout. A post on Reddit detailed a conversation with a Microsoft engineer who explicitly stated, “It is Tenant Lockout due to this MACE ninja rollout they did. No signs of compromise.” The engineer reassured the administrator that the issue would be resolved within an hour, converting the tickets from compromise statuses to lockout statuses.
A Systemic Flaw Exposed
The incident highlights a critical vulnerability in Microsoft Entra ID’s approach to credential detection. While MACE’s intention is noble—to protect users from credential leaks—it seems to lack robust safeguards against false positives. Organizations rely on their identity and access management systems to maintain trust and operational integrity. When these systems fail, the consequences can be devastating, disrupting workflows, eroding confidence, and potentially impacting business continuity.
Administrators who experienced the lockouts described the aftermath as both frustrating and exhausting. For many, the initial panic gave way to relief upon realizing the accounts weren’t actually compromised. However, the process of resolving the lockouts proved labor-intensive. Repeatedly unlocking accounts, verifying their status, and restoring access consumed valuable time and resources. Furthermore, the widespread nature of the issue meant that some organizations struggled to keep pace with the volume of requests.
Lessons Learned and Future Considerations
This incident serves as a wake-up call for both Microsoft and its enterprise customers. For Microsoft, the episode underscores the importance of thorough testing and quality assurance before rolling out new features like MACE. While automation and AI-driven tools offer immense potential, they must be implemented responsibly to avoid unintended consequences. Microsoft’s failure to publicly acknowledge the issue promptly has raised eyebrows, prompting questions about transparency and accountability in the tech industry.
For administrators, the incident reinforces the need for vigilant monitoring and proactive measures. While MACE is intended to enhance security, relying solely on automated alerts can be perilous. Human oversight remains essential in verifying the legitimacy of alerts and ensuring that false positives don’t spiral out of control. Additionally, organizations should consider implementing robust backup plans to mitigate the impact of similar incidents in the future.
Moving Forward
As the dust settles, the broader implications of this incident linger. Will Microsoft address the root cause of the false positives? Will they introduce safeguards to prevent recurrence? These questions remain unanswered, pending further communication from Microsoft. For now, administrators must remain cautious, scrutinizing alerts closely and leveraging their expertise to navigate such challenges.
The MACE Credential Revocation feature represents a significant step forward in credential detection, but its current shortcomings highlight the complexities of balancing security and usability. As enterprises increasingly depend on cloud-based identity solutions, ensuring their reliability becomes paramount. This incident serves as a stark reminder that even the most advanced technologies require careful calibration to fulfill their intended purpose.
The recent wave of account lockouts triggered by false positives in Microsoft Entra ID’s MACE feature has left a lasting impression on the IT community. While the problem appears to have been resolved, the lessons learned are invaluable. For Microsoft, this incident presents an opportunity to refine its approach to identity management and strengthen trust with its customers. For administrators, it underscores the importance of vigilance, preparedness, and a healthy dose of skepticism when dealing with automated alerts.
As we move forward, the tech landscape will continue to evolve, presenting new opportunities and challenges. By learning from incidents like this, organizations can better prepare for the inevitable bumps along the way. After all, the ultimate goal of identity management is not just to detect threats but to empower users while safeguarding their digital lives.













Add Comment