The dark web, a hidden corner of the internet, harbors a sea of information, both legitimate and malicious. It’s a place where personal data breaches can...
Cybersecurity
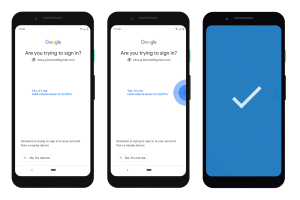
Two-factor authentication (2FA) has long been considered a critical defense against unauthorized access to online accounts. However, requiring both a password...
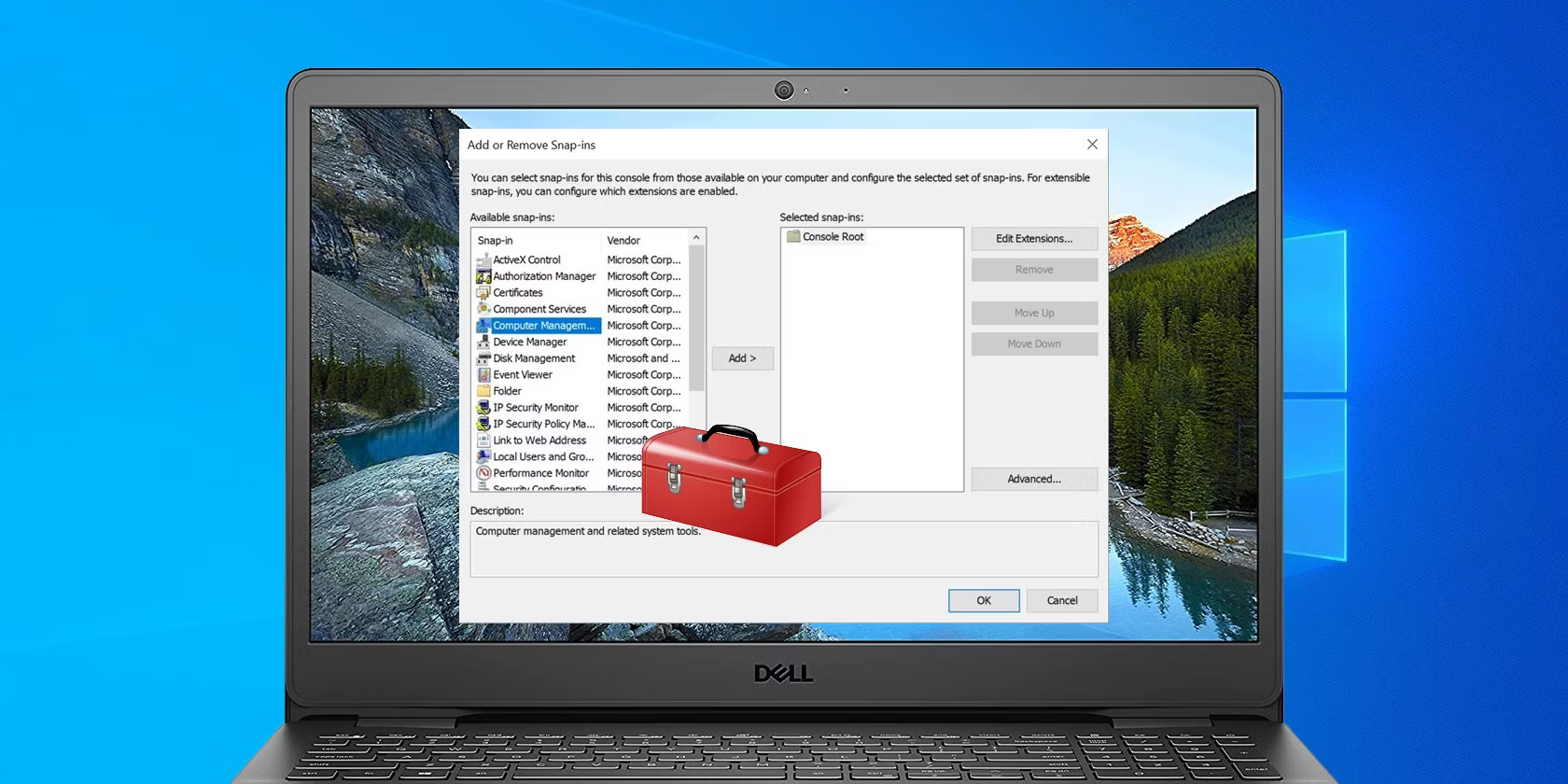
For system administrators, the Microsoft Management Console (MMC) is a familiar companion, offering a centralized hub for managing various Windows system...
A hacker known only as “Spider-Man” has exploited a vulnerability in Apple’s high-end Vision Pro headset. The exploit reportedly unleashed...
WhatsApp’s widespread popularity has, unfortunately, made it a fertile ground for scammers looking to exploit unsuspecting users. From impersonation to malware...