The year 2023 witnessed a significant shift in the cybersecurity landscape, marked by the emergence of new threats and innovative solutions. As organizations continue to grapple with the increasing complexity of digital threats, it’s crucial to stay informed about the latest trends and best practices. This article provides a comprehensive overview of the key cybersecurity trends that shaped the year.
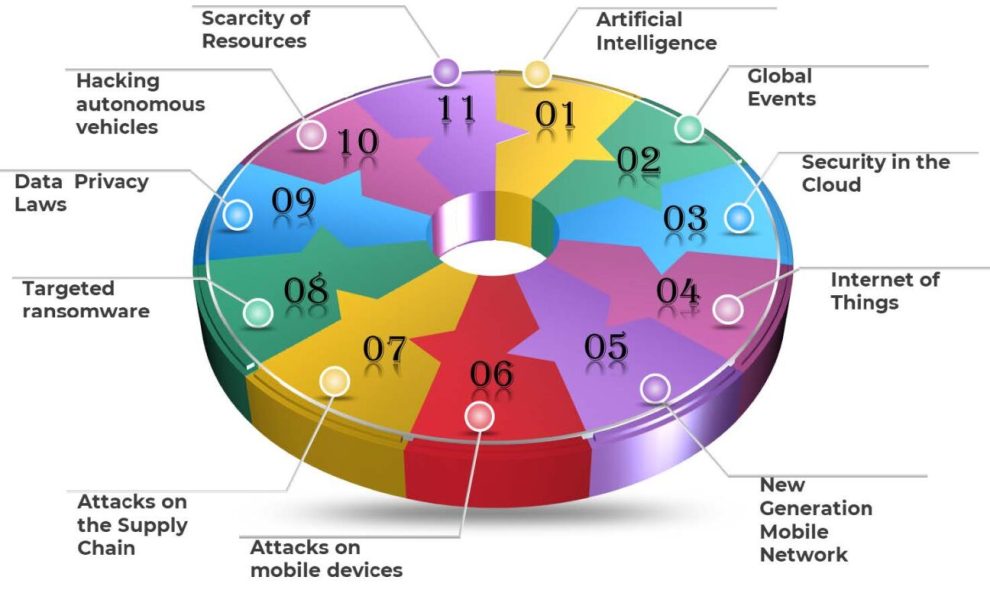
The Rise of AI-Powered Threats
- AI-driven phishing: Malicious actors are leveraging AI to create highly personalized phishing attacks that can bypass traditional detection methods.
- Deepfakes: AI-generated deepfakes are being used to spread misinformation and deceive individuals.
- Autonomous malware: AI-powered malware can adapt and evolve, making it more difficult to detect and eradicate.
The Growing Importance of Zero Trust Architecture
- Shifting paradigms: Zero trust architecture is gaining traction as organizations recognize the limitations of traditional perimeter-based security.
- Principle-based approach: This approach assumes that no one inside or outside the network should be trusted by default and requires strict verification for every access attempt.
- Benefits: Zero trust can help mitigate the risks associated with insider threats, data breaches, and supply chain attacks.
The Continued Threat of Ransomware
- Evolving tactics: Ransomware attacks continue to be a major concern, with attackers targeting critical infrastructure and demanding higher ransoms.
- Double extortion: A new trend involves attackers not only encrypting data but also threatening to publish stolen data if a ransom is not paid.
- Supply chain attacks: Ransomware attackers are increasingly targeting supply chain partners to gain access to their customers’ networks.

The Internet of Things (IoT) Security Crisis
- Vulnerable devices: IoT devices often have weak security measures, making them attractive targets for attackers.
- Botnets: IoT devices can be compromised and turned into botnets, which can be used for distributed denial-of-service (DDoS) attacks and other malicious activities.
- Regulatory scrutiny: Governments are increasing their focus on IoT security, leading to stricter regulations and standards.
The Impact of Cloud Migration
- Increased complexity: As organizations migrate more applications to the cloud, the complexity of their security landscape increases.
- Shared responsibility: Understanding the shared responsibility model between organizations and cloud providers is essential for effective security management.
- Cloud-native attacks: New types of attacks specifically targeting cloud-native technologies, such as serverless computing and containers, are emerging.
The Growing Threat of Insider Threats
- Malicious insiders: Employees with access to sensitive data can pose a significant threat to organizations.
- Accidental breaches: Even well-intentioned employees can inadvertently cause data breaches through mistakes or carelessness.
- Insider threat detection: Organizations must implement measures to detect and prevent insider threats, such as user behavior analytics and privileged access management.
The Rise of Cybersecurity as a Service (CaaS)
- Scalability and flexibility: CaaS offers organizations a scalable and flexible way to meet their cybersecurity needs.
- Cost-effective: CaaS can be more cost-effective than building and maintaining an in-house security team.
- Expertise: CaaS providers offer specialized expertise and knowledge of the latest threats and best practices.
The Importance of Cybersecurity Awareness
- Employee education: Educating employees about cybersecurity best practices is essential to prevent human error-based breaches.
- Phishing simulations: Conducting phishing simulations can help employees identify and report suspicious emails.
- Social engineering awareness: Training employees to recognize and avoid social engineering tactics is crucial.
The Role of Cybersecurity Insurance
- Risk mitigation: Cybersecurity insurance can help organizations mitigate the financial impact of a data breach.
- Incident response support: Insurers often provide incident response services to help organizations deal with breaches effectively.
- Risk management: Cybersecurity insurance can encourage organizations to implement stronger security measures.
In conclusion, the cybersecurity landscape continues to evolve rapidly, and organizations must stay informed about emerging threats and best practices. By understanding the key trends of 2023 and implementing appropriate security measures, organizations can protect their valuable data and minimize the risk of cyberattacks.















Add Comment