In the fast-changing landscape of cloud computing, security remains paramount. With sensitive data scattered across services and platforms, traditional access controls often fall short. This is where Identity and Access Management (IAM) plays a crucial role in locking down cloud environments.
Think of IAM as the gatekeeper, ensuring only authorized users and systems access the right resources. But effective IAM requires more than just passwords. It needs a strategic approach leveraging various components and advanced features.
This comprehensive guide will explore how to implement robust IAM for enhanced cloud security.
Laying the IAM Foundation: Core Principles
Before diving into specifics, let’s solidify understanding of these key principles:
- Least Privilege: Grant users the minimum permissions necessary. This limits damage from potential breaches.
- Zero Trust: Always verify users before granting access, regardless of location or previous permissions.
- Continuous Monitoring: Regularly review and audit activity to identify threats.
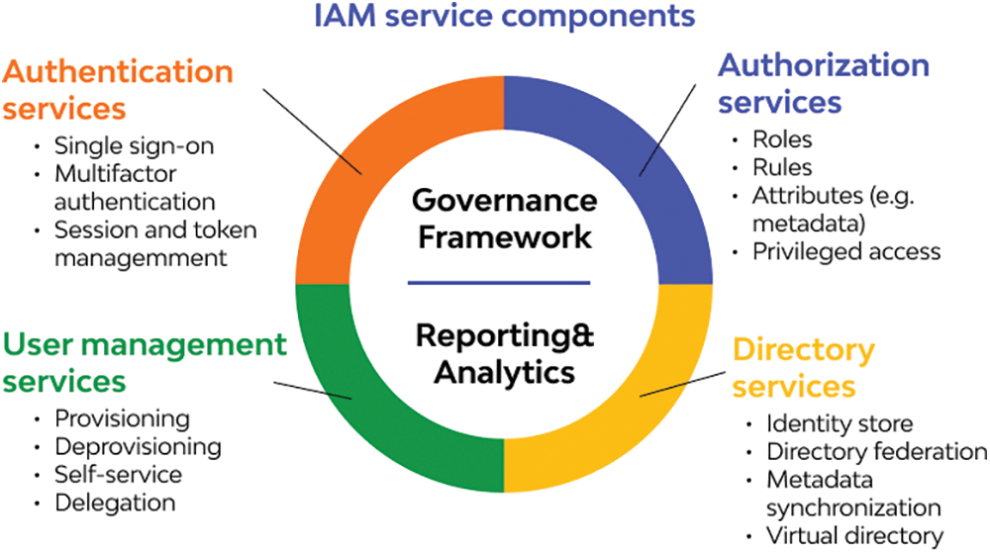
Building the IAM Infrastructure
Now let’s examine the essential components for building IAM defenses:
Strong User Authentication
Implement multi-factor authentication (MFA) for login. MFA requires users provide multiple verification factors, not just passwords. This adds an extra layer of security.
Granular Authorization
Define user roles then assign permissions based on those roles. Consider Role-Based Access Control (RBAC) to simplify managing permissions.
Access Control Lists
Create detailed access controls for specific resources, specifying who can access what and how.
Advanced IAM Strategies
For enhanced security, consider these additional IAM best practices:
Single Sign-On (SSO)
SSO enables single login access to multiple applications, improving convenience and security.
Identity Governance
Establishes policies and processes for managing users, ensuring compliance and best practices.
Privileged Access Management
Implements strict controls and monitoring for highly privileged accounts and sensitive resources.
Identity Federation
Allows users to authenticate with existing credentials to access cloud services, simplifying administration.
Choosing the Right IAM Solutions
Major cloud providers offer robust IAM services for user management, permissions, and activity monitoring. Top options include:
- AWS Identity and Access Management (IAM)
- Microsoft Azure Active Directory (AD)
- Google Cloud Identity and Access Management (IAM)
Select the solution best aligned to your cloud platform, security needs and budget.
Vigilant Maintenance is Key
IAM is not “set and forget.” Continuously monitor activity, audit access logs, and review permissions to identify threats. Regularly update credentials and policies to reflect personnel and requirement changes.
Remember, security is an ongoing process, not a destination. Frequently test defenses to address vulnerabilities. Seek expert assistance if needed – effective IAM can be complex.
By following these guidelines and leveraging IAM’s power, you can build a robust cloud security posture. A strong IAM strategy requires both technological and cultural shifts towards security awareness and best practices.
For even greater protection, explore emerging solutions like AI and machine learning. These can identify threats in real-time by detecting abnormal behavior.
Implementing comprehensive IAM takes cloud security to the next level. Use this guide to lock down your cloud environment with identity-centric defense.















Add Comment