Ivanti Neurons has established itself as a powerful contender in the enterprise security and device management space. With nearly four decades of industry experience and serving over 40,000 customers worldwide, Ivanti’s platform represents a sophisticated approach to managing and securing corporate IT infrastructure in 2024.
At its core, Ivanti Neurons differentiates itself through its intelligent approach to risk management and security automation. Unlike traditional remote management and monitoring (RMM) solutions that rely primarily on human validation of security threats, Ivanti employs a more nuanced and comprehensive methodology through its Vulnerability Risk Rating (VRR) system. This sophisticated approach combines multiple security frameworks, including Common Weakness Enumeration (CWE) data, open-source threat intelligence, and OWASP standards, to generate a precise risk score between 0 and 10.
The platform’s emphasis on risk-based patch management represents a significant advancement over conventional approaches. Rather than treating all security vulnerabilities with equal urgency, Ivanti Neurons prioritizes patches based on their actual threat level, ensuring that IT teams can address the most critical security risks first. This strategic approach becomes increasingly valuable as organizations face an ever-expanding array of potential security threats across their digital infrastructure.
One of Ivanti Neurons’ most compelling features is its comprehensive device support across multiple operating systems and platforms. The solution seamlessly manages everything from Windows and macOS devices to iOS and Android mobile platforms, addressing the growing complexity of modern workplace device ecosystems. This versatility is particularly relevant as organizations continue to navigate hybrid work environments where employees use various devices and operating systems.
The platform’s Unified Endpoint Management (UEM) capability provides IT administrators with a centralized view of all endpoints, streamlining the entire device lifecycle management process from initial deployment to eventual retirement. This single-pane visibility proves invaluable for organizations managing large-scale device deployments, especially those with remote workforces.
Ivanti has shown particular foresight in its approach to Bring Your Own Device (BYOD) policies, offering a dedicated portal that enables employees to integrate personal devices into the corporate infrastructure without compromising security. This feature becomes increasingly relevant as the lines between personal and professional device usage continue to blur in modern workplaces.
The platform’s application control capabilities are equally impressive, offering granular management of user privileges across Windows, Windows Server, and Linux systems. The implementation of Trusted Ownership checking provides an additional layer of security against zero-day malware by verifying the NTFS owner of applications before execution. This approach to privilege management allows organizations to maintain tight control over application access while minimizing endpoint vulnerability and associated security costs.
While Ivanti Neurons offers powerful functionality, its interface reflects a pragmatic approach to enterprise software design. The dashboard system is role-based, ensuring users only see information relevant to their responsibilities. The extensive use of color-coded charts, graphs, and pivot tables facilitates quick data interpretation, though some users might find the overall aesthetic somewhat dated compared to more modern alternatives.
The platform’s security credentials are substantial, with certifications including SOC2 and ISO/IEC 27001 compliance. Ivanti’s active compliance with GDPR regulations and maintenance of a dedicated data privacy team demonstrates a serious commitment to data protection. Regular penetration testing further reinforces the platform’s security posture.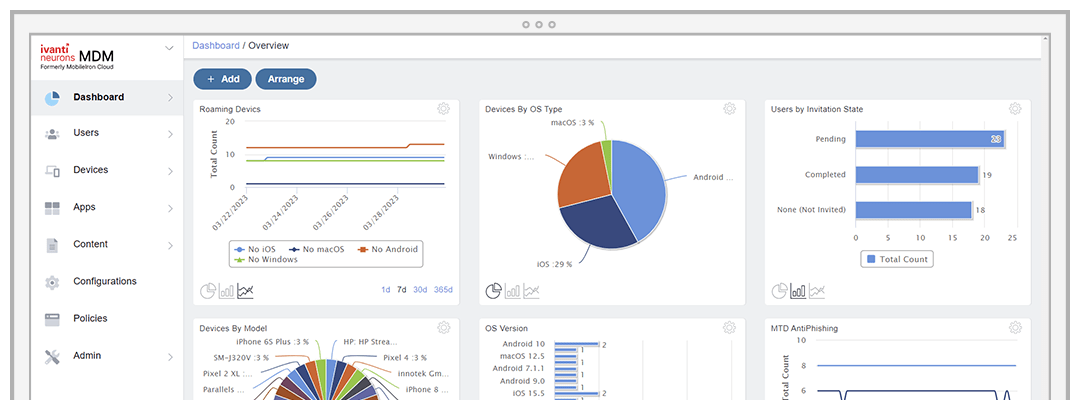
Customer support represents another strong point for Ivanti Neurons, with a sophisticated tiered support system that includes 24/7 callback options for critical issues. The platform’s community forums are particularly well-organized, featuring product-specific groups and designated MVP members who provide expert guidance. This comprehensive support infrastructure can prove crucial for organizations deploying complex security solutions across large networks.
However, potential adopters should be aware of certain considerations. The platform’s complexity, while offering powerful capabilities, may require significant training investment for new users. Additionally, Ivanti’s custom pricing model, while allowing for tailored solutions, makes it difficult for organizations to quickly compare costs with alternative solutions without engaging with the sales team.
Looking toward the future, Ivanti’s recent introduction of AI-powered automations for endpoint patching and technical issue management through behavioral analysis suggests a commitment to leveraging emerging technologies. This integration of artificial intelligence could prove increasingly valuable as organizations face growing cybersecurity challenges and resource constraints.
For large enterprises seeking a comprehensive security and device management solution, Ivanti Neurons presents a compelling option. The platform’s sophisticated risk assessment methodology, broad device support, and robust security features make it particularly suitable for organizations with complex IT infrastructures and stringent security requirements. While the learning curve may be steep and pricing negotiations potentially time-consuming, the platform’s comprehensive capabilities and strong support infrastructure can justify these initial hurdles for organizations prioritizing security and operational efficiency in their IT operations.















Add Comment