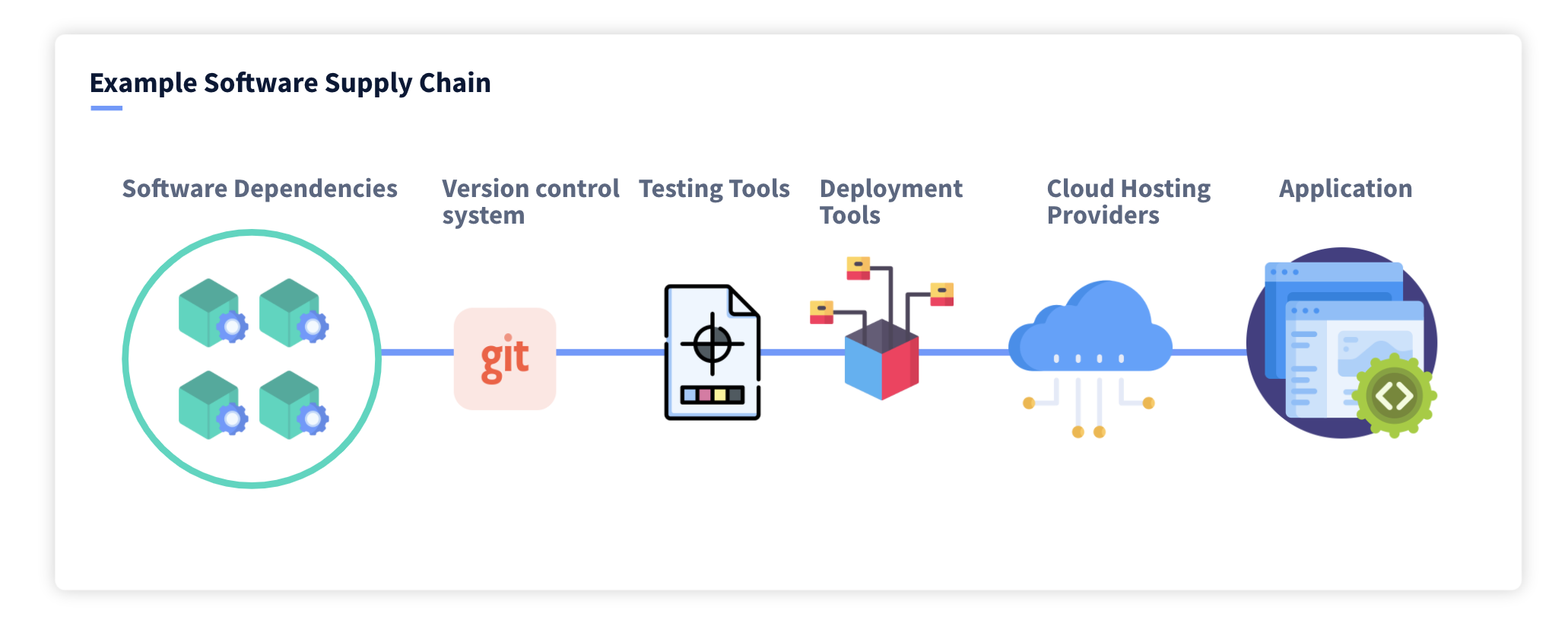
The software world runs on dependencies – libraries, frameworks, and modules that form the building blocks of countless applications. Among these, open-source dependencies play a crucial role, democratizing development and accelerating innovation.
But amidst this collaborative utopia lurks a dark secret: software supply chain attacks, leveraging compromised open-source dependencies to wreak havoc across entire ecosystems.
The Poisoned Well: How Dependencies Become Weapons
Imagine a hacker injecting malicious code into a widely used open-source library. Suddenly, thousands of applications relying on that library become vulnerable. A single poisoned well can contaminate countless downstream applications, leading to:
- Data Theft: Malicious code can siphon sensitive user data, credit card information, or trade secrets from infected applications.
- Ransomware Outbreaks: Backdoors inserted into dependencies can be used to launch coordinated ransomware attacks against multiple applications simultaneously.
- System Disruption: Injected code can manipulate application functionalities, causing crashes, outages, and operational breakdowns.
- Loss of Trust: When a widely used dependency is compromised, the entire ecosystem suffers a blow to trust, impacting all the applications and businesses built upon it.
The Attacker’s Toolbox: From Code Tampering to Social Engineering
These supply chain attacks are not mere fantastical exploits; they represent a growing threat with a diverse arsenal:
- Code injection: Hackers sneak malicious code into open-source libraries through vulnerabilities or during the development process.
- Fake packages: Deceptively named or poorly reviewed packages lure developers into using compromised versions of legitimate libraries.
- Man-in-the-middle attacks: Malicious actors intercept software updates or downloads, injecting malware into dependencies before they reach users.
- Social engineering: Phishing and other social engineering tactics are used to trick developers into downloading and installing compromised dependencies.
Building a Wall Around the Well: Mitigating Supply Chain Risks
Defending against these attacks requires a layered approach:
- Vetting Dependencies: Choose reputable sources for your dependencies, carefully review code and security audits before integration.
- Minimizing Dependencies: Limit the number of dependencies your application uses, reducing the attack surface and simplifying maintenance.
- Continuous Monitoring: Monitor your dependencies for updates and vulnerabilities, ensuring timely patching and remediation.
- Secure Development Practices: Implement secure coding practices throughout your development lifecycle, from code reviews to vulnerability scanning.
- Collaboration and Transparency: Foster collaboration within the open-source community, promote security best practices, and report vulnerabilities promptly.
Key Factors Driving Software Supply Chain Attacks
Several interlocking factors create the perfect storm for software supply chain attacks to proliferate and succeed:
- Exponential Growth in Software Dependencies: Modern applications rely on dozens, sometimes hundreds of different dependencies – expanding the attack surface.
- Limited Developer Awareness: Many developers fail to fully grasp and mitigate risks from incorporating unvetted 3rd party code.
- Weak Auditing Practices: Open source projects often lack resources for extensive security reviews leaving backdoors undiscovered.
- Automation Driving Scale: Tools like automated build pipelines enable supply chain attacks launched against one target to infect thousands nearly instantly.
Inside Devastating Real-World Attacks
Software supply chain attacks moved from theoretical to reality in recent years through incidents like:
- SolarWinds Breach: Russian hackers trojanized network management software updates to breach US government agencies and Fortune 500 companies.
- Codecov Bash Uploader Attack: Hackers backdoored the Bash Uploader utility allowing theft of sensitive credentials and keys from 29+ organizations.
- npm Malicious Packages: Over 700 malicious JavaScript packages on the npm registry were caught stealing environment variables and credentials.
Each attack leveraged different tactics – but used trusted open source dependencies as the vehicle to bypass traditional perimeter defenses.
The Inevitable Open Source Dependency Dilemma
Given the pivotal role open source plays in accelerating software innovation, we cannot simply abandon dependencies. The challenge is managing risk while preserving openness.
Organizations struggle to balance:
- Deriving competitive advantage from open source innovation
- Protecting themselves from open source supply chain threats
The most effective approach combines diligent oversight of dependencies with fostering transparency across the open source community.
The Future of Dependency Management: Building a Trusted Ecosystem
Software supply chain attacks are a wake-up call, urging us to re-evaluate how we build and manage dependencies. As we move forward, we must:
- Develop secure by design tools and frameworks: Embed security considerations into dependency management tools and open-source development platforms.
- Invest in automated vulnerability detection and response: Leverage AI and machine learning to automate vulnerability detection and mitigation within dependencies.
- Promote transparency and collaboration: Fostering a culture of openness and information sharing within the open-source community is key to building trust and detecting threats early.
By acknowledging the risks, adopting best practices, and fostering collaboration, we can transform the vulnerable veins of software supply chains into pathways of reliable, secure applications – safeguarding the very foundation of our digital world.
















Add Comment