A highly sophisticated scam operation has emerged, targeting Gmail users with an elaborate scheme designed to hijack their accounts. This latest cyber threat employs a potent combination of artificial intelligence, spoofed Google phone numbers, and meticulously crafted email communications to dupe unsuspecting victims into surrendering control of their digital lives.
The Anatomy of the Scam
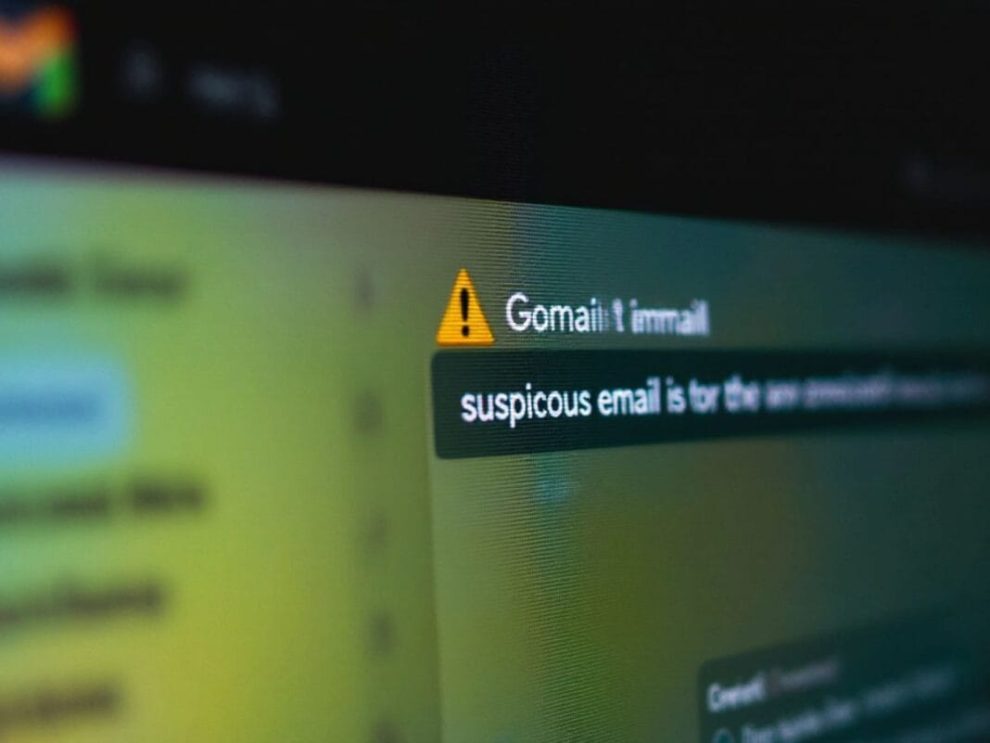
The scam begins innocuously enough, with targets receiving what appears to be an official email from Google. These messages are masterfully crafted, mimicking Google’s branding, tone, and formatting to near perfection. The email typically alerts the user to a purported security issue with their Gmail account, urging immediate action to prevent loss of access.
What sets this scam apart from run-of-the-mill phishing attempts is the next step: a phone call from an apparent Google support representative. Here’s where the criminals’ sophisticated approach becomes evident:
- AI-Powered Voice Synthesis: The “representative” on the call isn’t human at all, but an artificial intelligence using advanced voice synthesis technology. This AI voice is often indistinguishable from a real person, complete with natural-sounding speech patterns and the ability to respond contextually to basic queries.
- Spoofed Google Phone Numbers: The incoming calls appear to originate from legitimate Google support phone numbers, lending an air of authenticity that can fool even tech-savvy individuals.
- Social Engineering Tactics: The AI is programmed with an array of social engineering techniques, designed to build trust and create a sense of urgency that compels victims to act quickly without thoroughly considering the implications.

The Takeover Process
Once engaged with the target, the scammer’s AI guide walks the victim through a series of steps ostensibly aimed at “securing” their account. In reality, these actions grant the attackers full access to the Gmail account and, potentially, a wealth of sensitive information contained within.
Some of the common tactics employed include:
- Directing users to change their password to a “temporary” one provided by the scammer
- Requesting the user to disable two-factor authentication “for testing purposes
- Guiding victims to grant access to third-party apps controlled by the attackers
- Instructing users to forward copies of all emails to a “secure” address for “backup
The Aftermath
The consequences of falling victim to this scam can be devastating. Once in control of a Gmail account, scammers gain access to a treasure trove of personal and potentially sensitive information. This can include:
- Personal and professional correspondence
- Financial documents and statements
- Password reset capabilities for other online accounts
- Contact lists that can be exploited for further scams
Moreover, the compromised Gmail account can serve as a launchpad for additional attacks, with scammers using the victim’s identity to target their contacts or engage in broader phishing campaigns.
Expert Reactions
Cybersecurity experts are sounding the alarm about the sophistication and potential widespread impact of this scam. Dr. Eliana Frost, Chief Information Security Officer at CyberShield Solutions, warns, “This represents a quantum leap in the complexity and believability of phishing attacks. The integration of AI-driven voice technology with traditional email phishing creates a multi-pronged assault that can confound even the most security-conscious individuals.”
Mark Reardon, a senior threat analyst at Digital Fortress Inc., adds, “What’s particularly concerning is the scammers’ use of actual Google phone numbers and seemingly official email addresses. This level of detail in the impersonation makes it incredibly challenging for the average user to distinguish between legitimate communications and this scam.”
Google’s Response
Google has acknowledged the threat and is actively working to combat it. A company spokesperson stated, “We are aware of this sophisticated impersonation scheme and are implementing additional security measures to protect our users. We want to emphasize that Google will never call users unprompted to ask for account credentials or sensitive information.
The tech giant is urging users to be vigilant and has outlined several steps to help identify and avoid such scams:
- Be skeptical of unsolicited communications, even if they appear to come from Google.
- Never provide account passwords or disable security features based on phone or email requests.
- Verify the authenticity of communications by contacting Google through official channels listed on their website.
- Enable additional security features like Advanced Protection for high-risk users.
Protecting Yourself
In light of this evolving threat, cybersecurity experts recommend the following steps to safeguard your Gmail account and digital identity:
- Enable Strong Two-Factor Authentication: Use app-based or hardware security keys rather than SMS-based verification.
- Regularly Review Account Activity: Check your Gmail security settings for any unauthorized access or suspicious app permissions.
- Use Unique, Complex Passwords: Employ a password manager to create and store strong, unique passwords for each online account.
- Be Wary of Urgent Requests: Legitimate companies rarely demand immediate action regarding account security via email or phone.
- Educate Yourself and Others: Stay informed about the latest scam techniques and share this knowledge with friends and family.
- Implement Advanced Security Features: Consider enrolling in Google’s Advanced Protection Program if you’re at higher risk of targeted attacks.
The Broader Implications
This Gmail takeover scam is more than just another cybersecurity threat; it represents a worrying convergence of advanced technologies in the hands of malicious actors. The use of AI-powered voice synthesis, in particular, opens up new avenues for scammers to exploit human trust and circumvent traditional security measures.
We’re entering an era where the line between genuine and fake communications is increasingly blurred,” notes Dr. Frost. This necessitates a fundamental shift in how we approach online security and verify digital identities.
The incident also highlights the ongoing arms race between cybercriminals and security professionals. As defensive technologies evolve, so too do the tactics of those seeking to exploit vulnerabilities in both systems and human psychology.
As news of this scam spreads, it’s likely that variations will emerge, potentially targeting users of other email providers or expanding to impersonate different trusted entities. This underscores the need for constant vigilance and adaptability in the face of evolving cyber threats.
Reardon of Digital Fortress Inc. predicts, “We’ll likely see an uptick in AI-assisted scams across various platforms. The technology is out there, and unfortunately, it’s only a matter of time before it becomes more widely adopted by cybercriminal networks.”
In response, both tech companies and cybersecurity firms are ramping up efforts to develop more robust authentication methods and AI-powered defensive tools. These may include advanced voice recognition systems capable of detecting synthesized speech and machine learning algorithms designed to identify and flag suspicious patterns of account activity.
The emergence of this sophisticated Gmail takeover scam serves as a stark reminder of the ever-present dangers lurking in our increasingly digital world. It underscores the critical importance of remaining vigilant, skeptical of unsolicited communications, and proactive in safeguarding our online identities.
As the battle between scammers and security experts intensifies, individual users represent both the last line of defense and the most vulnerable targets. By staying informed, implementing strong security practices, and approaching online interactions with a healthy dose of caution, we can collectively work to mitigate the impact of these evolving threats.
In the end, the best defense against such sophisticated scams may well be a combination of technological safeguards and good old-fashioned common sense. As we navigate this new landscape of AI-enhanced deception, maintaining a critical eye and a questioning mind will be more crucial than ever in protecting our digital lives from those who seek to exploit them.














Add Comment